ShieldIOT enables service providers, IoT brands and integrators to secure large complex connected device networks. Explore how ShieldIOT automatically detect the first signs of cyber attacks and operational events.
Send us your details and a ShieldIOT representative will provide you with your free 30 day license.
With X9 more IoT cyber-attacks in 2019, unknown malware, DDoS and ransomware attacks represent an escalating threat to critical IoT networks, leading to brand damage, privacy and data theft, massive financial losses and even loss of life.
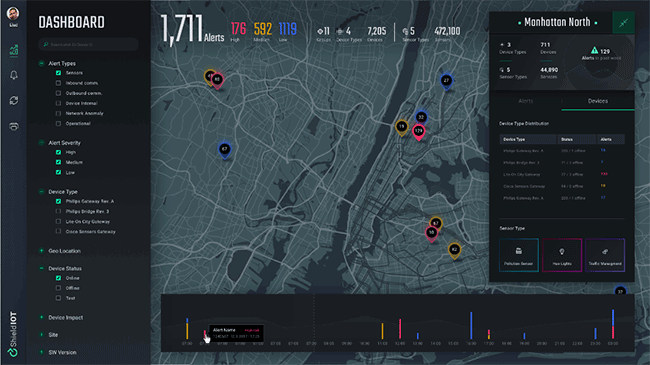
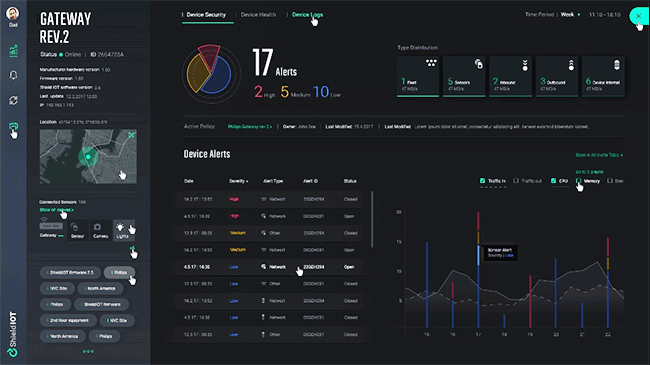
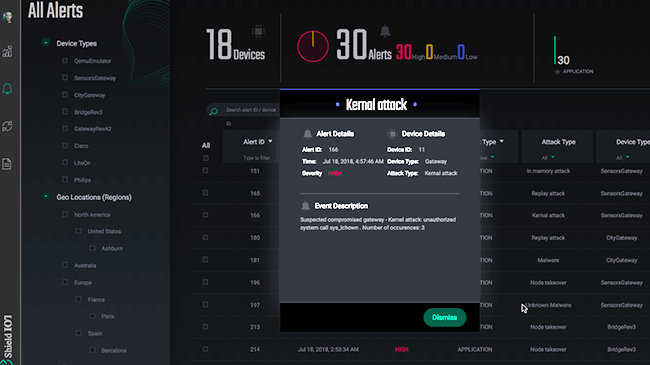
Get direct access to ShieldIOT platform functionality, including multi-layer device-level protection, combined with cloud-based centralized management and control.
Shield-IoT is a cybersecurity software solution provider securing cellular IoT/IIoT networks. Based on 15 years of Coreset-AI academic research (MIT), Shield-IoT patented agent-less AI Asset Intelligence and Threat Management SaaS platform helps meet compliance standards, and provides IoT visibility and security, across any SIM-connected device and application, at unlimited scale. With Shield-IoT, Telcos and IoT service providers can now offer a bundled/value-add IoT security service on top of connectivity to create differentiation, win new business and generate new revenue streams.

For more information about Shield-IoT solutions, send us an email and a Shield-IoT expert will contact you.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |