Detect the first signs of unknown cyber-attacks and operational events to safeguard device data, operations, and critical services before any damage occurs.
Mobile and IoT security risks are on the rise. Verizon reports that 53% of IoT device users in critical infrastructure sectors have experienced severe security incidents that resulted in data loss or system downtime, with recent researchers report a 400% increase in IoT malware attacks.
Example of detected threats include unknown malware, DDoS, device takeover, IoT ransomware attacks, communication hijacking, cloud hacking, data theft, device abnormal usage, device malfunction, SIM switch, SIM abuse and more. Such attacks can result in compromise of personal information, data theft, service disruption, downtime and even hacking the enterprise in which compromised devices are used as an entry point for attackers to penetrate the organization.
Securing IoT devices is challenging considering the massive scale of IoT networks, with potentially thousands or even millions of devices, as can be found today in transportation, smart grids, smart city and payment networks. The sheer variety of device types and applications complicates security efforts, as each device may have different behavior, internal resources, vulnerabilities, and requirements.
Another common challenge is that many IoT devices were not originally designed with security in mind, leaving them susceptible to attacks. A shortage of IoT security expertise makes matters worse, as traditional IT security practices do not always translate effectively to the IoT landscape.
But the significant challenge organizations face is that majority of these devices are exposed in the field, operating outside traditional enterprise network perimeter defenses, leading to significant visibility gaps, making them vulnerable to physical tampering and remote attacks.
Addressing these challenges is essential for preventing security incidents and protecting the integrity of IoT deployments.
Detect the first signs of unknown cyberattacks and operational anomalies.
Per detected event provide:
The Threat Management Module includes 3 main detection engines, that analyze network traffic statistics, to provide early accurate detection of any known or unknown, network-based, cyber-attacks or operational events.
Continuously learns normal device behavior to accurately detect unknown cyber-attacks and operational anomalies. Based on patented industry-first Coreset-AI technology and over 15 years of academic research in MIT and Haifa University.
Detects various known cyber-attacks and operational events, using both system predefined and user-based rules. Includes over 140 pre-built security rules as well as a unique user-based rule wizard, enabling to create new rules in minutes, with no need for any coding or technical expertise.
Identifies communication with known malicious sites and suspicious destinations. Combines internal Shield-IoT research with over 100 external threat intelligence feeds, all updated in real-time, to provide an extensive IoT security threat intelligence feed.
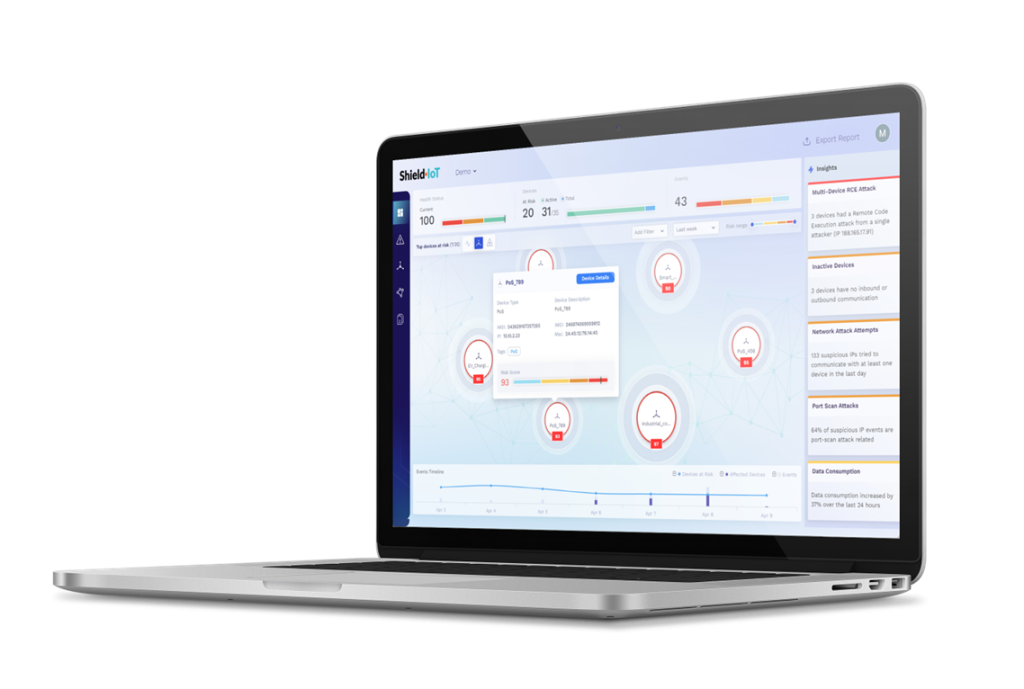
To immediately understand what happened and take any necessary actions. Event forensic information includes the relevant device ID, event type, severity, triggers/parameters that led to the creation of the event, link to the raw data PCAP/NetFlow file for event validation and investigation, and recommended action.
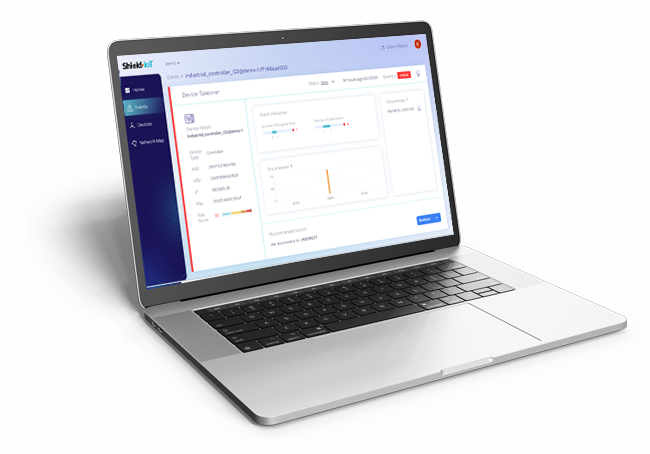
Shield-IoT provides the industry-first Coreset-AI anomaly detection solution, analyzing device network traffic statistics (metadata), to accurately detect in real-time unknown cyber-attacks and operational events.
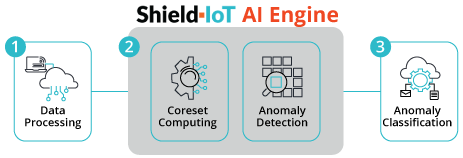
The incoming data is automatically processed (data cleaning, aggregations, feature engineering etc.) and sent to the AI engine for analysis
Coreset compression to reduce the data by a factor of nearly 1000, followed by running a set of AI and unsupervised machine learning anomaly detection algorithms
Automatically determine event type, by combining patented supervised clustering-based labeling process and deep learning with embedded domain expertise
Enabling manual or automatic threat prevention actions together with the ability to export all system information and findings to customer third party systems.
Generate an appropriate response to cyberattacks, misusage, and operational events.
Prevention is done by combining real-time actionable alerts (alerting on the event type and recommended action) with existing customer third party prevention tools, such as the connectivity management platform, or any other network segmentation/control tool.
The platform empowers any preventive action supported by existing customer third-party control systems, including blocking communication with suspicious IPs, throttling traffic during a DDoS attack, redirecting traffic to a secure APN, and even isolating compromised devices to prevent them from interacting with malicious actors or threatening the enterprise. Prevention can be executed manually through user-initiated actions, such as pressing a button in the UI, or automatically via pre-defined security policies.
All system information, including monitored devices, detected events, network insights and generated reports, can be exported to any 3rd party systems via Push or Pull functionality.
Fully customizable Push templates enable to export events (for example to customer’s SIEM) and apply preventive actions (for example to CSP’s connectivity management platform) via HTTP or SMTP. This approach not only enables to export events/actions in real-time, but doesn’t require any efforts (e.g. build scripts) on the customer side.
Comprehensive Pull RESTFul Open API enables to export any/all system information to any 3rd party system (SIEM, management, ticketing…). It enables to read/create/update any entity in the system (such as manage users, create rules, update device information etc.) as well as execute complex queries (such as query events or devices, fetch device data consumption or events distribution over time etc.).