GATEWAY SECURITY
Prevent 99% of events before any damage can take place.
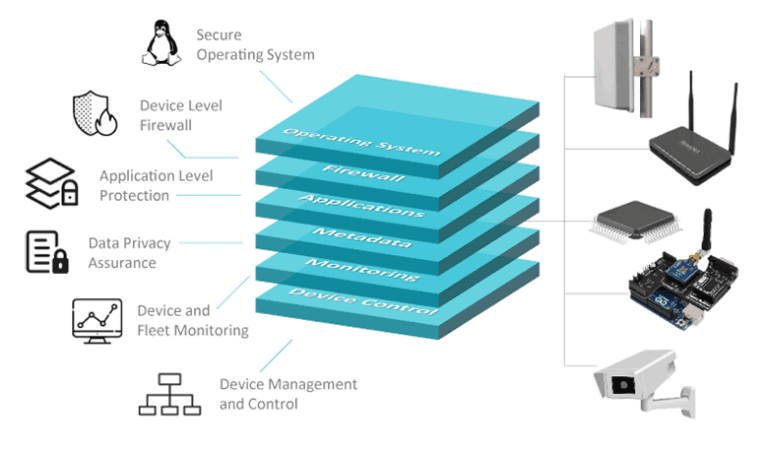
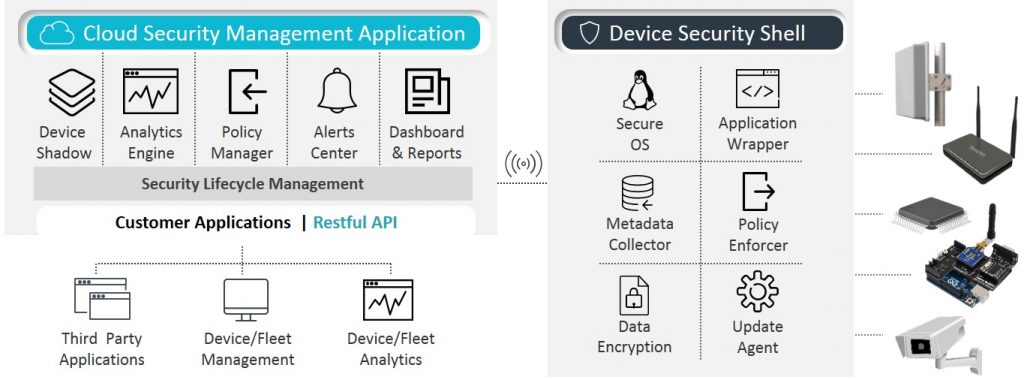
The ShieldIOT solution includes multiple layers of security and is ideal for protection of gateways, industrial PCs and Linux-based edge devices. ShieldIOT prevents damage to device operation and safeguards connected IoT network components. The software solution includes a device-level security agent responsible for ongoing automatic protection, with a centralized security management application to be used by the IoT network operator, to easily manage the device and fleet alerts, policies, updates and overall security.