Monitor and secure any out-of-perimeter connected device across any IoT/IIoT application at any scale.
Protect any out-of-perimeter IoT device, application or network with an agent-less, context-free anomaly detection solution
Automatically mitigate any threats with real-time accurate event detection combined with rich actionable alerts
Secure millions of connected devices with patented technology enabling accurate analytics at mass scale
Shield-IoT analyzes device-to-cloud traffic statistics and displays detected security events and operational anomalies on a multi-tenant dashboard or via third party systems through REST API.
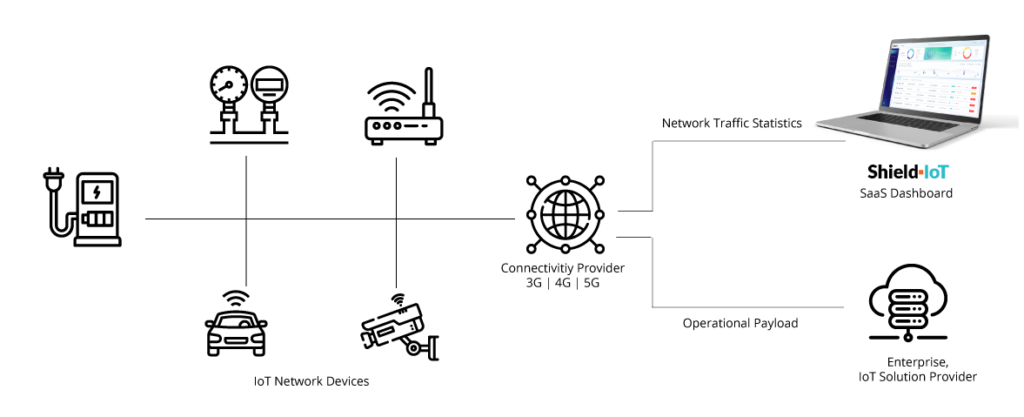

Prevent service impact or downtime with early detection of security events.
Secure millions of connected devices with patented technology enabling accurate analytics at mass scale.
Ensure no impact on existing operations with out-of-band SaaS solution.
Built to protect evolving IoT networks with always-up-do-date machine learning capabilities.

Shieild-IoT software solutions are deployed across a wide range of industry use cases and applications. Our purpose-built IoT security management solution provides continuous threat mitigation with no changes to your network.

Shield-IoT is a cybersecurity software solution provider securing cellular IoT/IIoT networks. Based on 15 years of Coreset-AI academic research (MIT), Shield-IoT patented agent-less AI Asset Intelligence and Threat Management SaaS platform helps meet compliance standards, and provides IoT visibility and security, across any SIM-connected device and application, at unlimited scale. With Shield-IoT, Telcos and IoT service providers can now offer a bundled/value-add IoT security service on top of connectivity to create differentiation, win new business and generate new revenue streams.

For more information about Shield-IoT solutions, send us an email and a Shield-IoT expert will contact you.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |