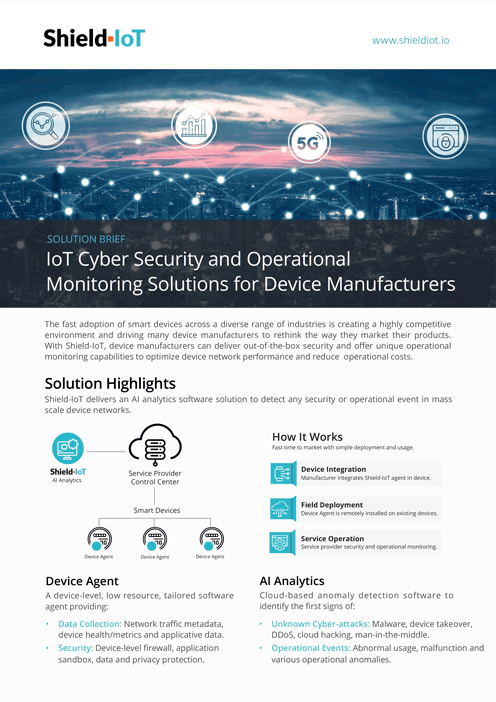
VALUE PROPOSITION
Shift to Solution-based Offering with Security and Operational Monitoring.
Protect against any unknown cyber threats, on any mass scale industrial device network, with cloud-level AI anomaly detection combined with gateway-level threat prevention.
AI Analytics
Device Agent
AI Analytics
Cloud-based AI analytics anomaly detection software solution, analyzing device and network collected data, to accurately detect the first signs of any unknown cyber attacks or operational events, enabling cyber threat prevention and operational predictive analytics.
- Unknown cyber attacks: detect any device and network based cyber attacks
- Operational events: detect device abnormal usage, faults and operational anomalies
Device Agent
Light, low-resources, device-level software agent solution (optional). Tailored to manufacturer gateway resources and applications. The agent performs data collection for any gateway type and includes device-level multi-layered threat prevention (for Linux gateways).
- Data Collector (AI-enabler): device traffic metadata, device health/metrics, applicative data.
- Gateway Security (applicable for Linux devices): network firewall, application sandbox, privacy and data protection.