The ShieldIOT solution includes multiple layers of application-level security and is ideal for protection of gateways, industrial PCs and Linux-based edge devices. ShieldIOT prevents damage to device operation and safeguards connected IoT network components. The uniqueness of ShieldIOT is that all components (including gateways, devices and sensors) continue to work even when compromised.
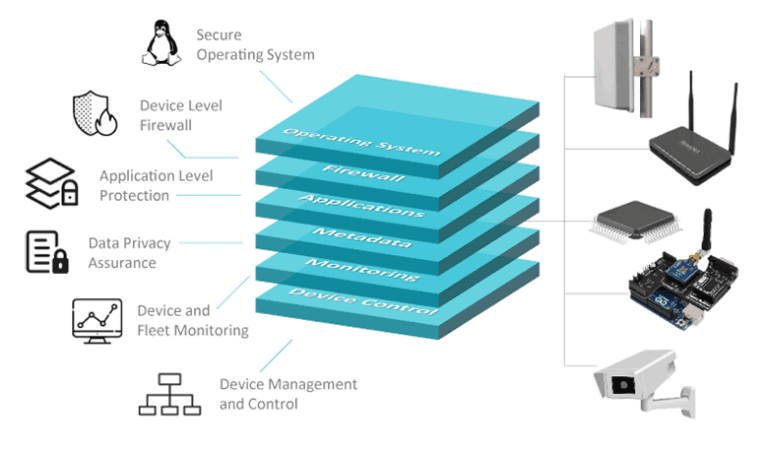

Production-ready, linux-based operating system with dynamic defenses, minimal attack surface and automatic security updates

Prevent device hacking, data theft and DDoS attacks with automatic prevention of unauthorized communication with IP addresses, ports, protocols

Over 70 protection types including application and process isolation, protection of key resources and sensitive system directories.

Smart granular encryption of sensitive data-at-rest including personal information, confidential records and device certificates

Collection and analysis of device metadata to detect anomalous activity and ensure complete visibility for all fleet security/operational events
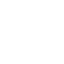
Centralized intuitive tag-based policy configuration, distribution and enforcement for all device security mechanisms

Manage device activities, monitor device status and metadata including logs, health traffic and alerts.

Create and update device security firewall application and operational policies.

Monitor, drill-down and investigate security and operational alerts for all fleet devices.
Aggregate and analyze device logs and information to detect fleet-wide anomalies.

Display detailed drill down data for fleet entities, device types and locations etc.

Deploy secure images, update and deploy OS application, alerts and policies.
Shield-IoT is a cybersecurity software solution provider securing cellular IoT/IIoT networks. Based on 15 years of Coreset-AI academic research (MIT), Shield-IoT patented agent-less AI Asset Intelligence and Threat Management SaaS platform helps meet compliance standards, and provides IoT visibility and security, across any SIM-connected device and application, at unlimited scale. With Shield-IoT, Telcos and IoT service providers can now offer a bundled/value-add IoT security service on top of connectivity to create differentiation, win new business and generate new revenue streams.

For more information about Shield-IoT solutions, send us an email and a Shield-IoT expert will contact you.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |